Palo Alto Firewall
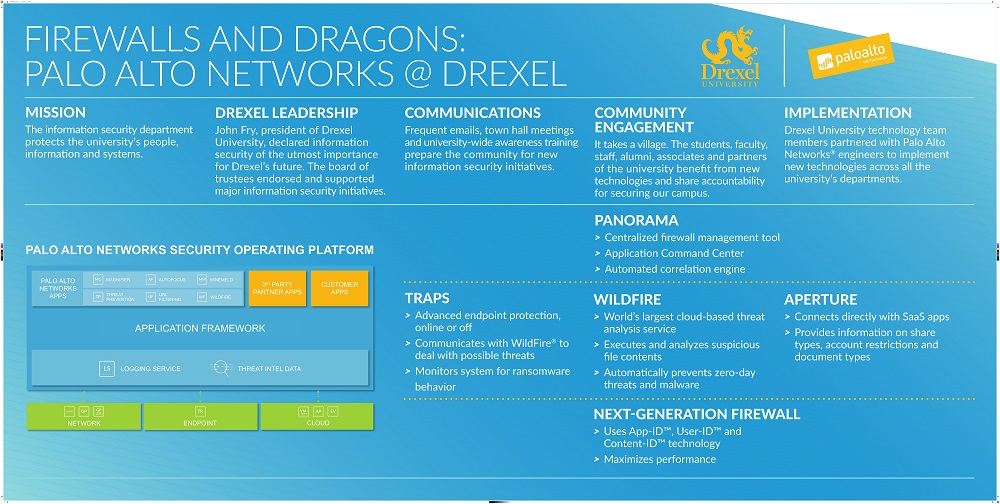
To improve its cyber defenses, Drexel University recently embarked in a multi-year project to install advanced firewalls and other state-of-the-art protection technologies made by Palo Alto. Drexel University IT operated the border firewall on select campus networks throughout 2018. The expected completion date for the first phase of the project, protecting all campus buildings against internet threats, is December 31st, 2018. If you think that you are experiencing a problem caused by the border firewall, please contact your local IT support team or the Drexel University IT Help Desk at https://drexel.edu/it/services/catalog/helpdesk/.
- The border firewall becomes an important part of the tools that Drexel University IT deploys to defend the campus against cyber attacks originating from the internet. These attacks are designed to gain unauthorized access to University computing resources, to modify or disclose University data, to steal or consume resources, or to disrupt the operation of the University.
- The border firewall does not impact the normal flow of data, e.g., academic or research traffic, because it operates by blocking well known security threats, attack vectors, and traffic to well-known malicious or dangerous sites. If the border firewall detects that a computer’s web traffic is destined for a known malicious site that could compromise campus security, the computer will show a web page indicating that access is blocked.
- The border firewall does not introduce any new traffic blocking policies or perform censoring of traffic content. Its function is focused on blocking access to identifiable and known security threats that put the campus at risk. The border firewall’s detection engine is updated in real-time by trusted sources around the world and it performs careful inspection of known attack vectors.
This is a state-of-the art technology operated by Drexel University IT with guidance and support provided by the manufacturer. The border firewall is not a replacement for security configurations or protection tools installed on your computer. The best cyber security is built with multiple layers of protection and the border firewall is just another important tool used to protect you and the University. Be safe.